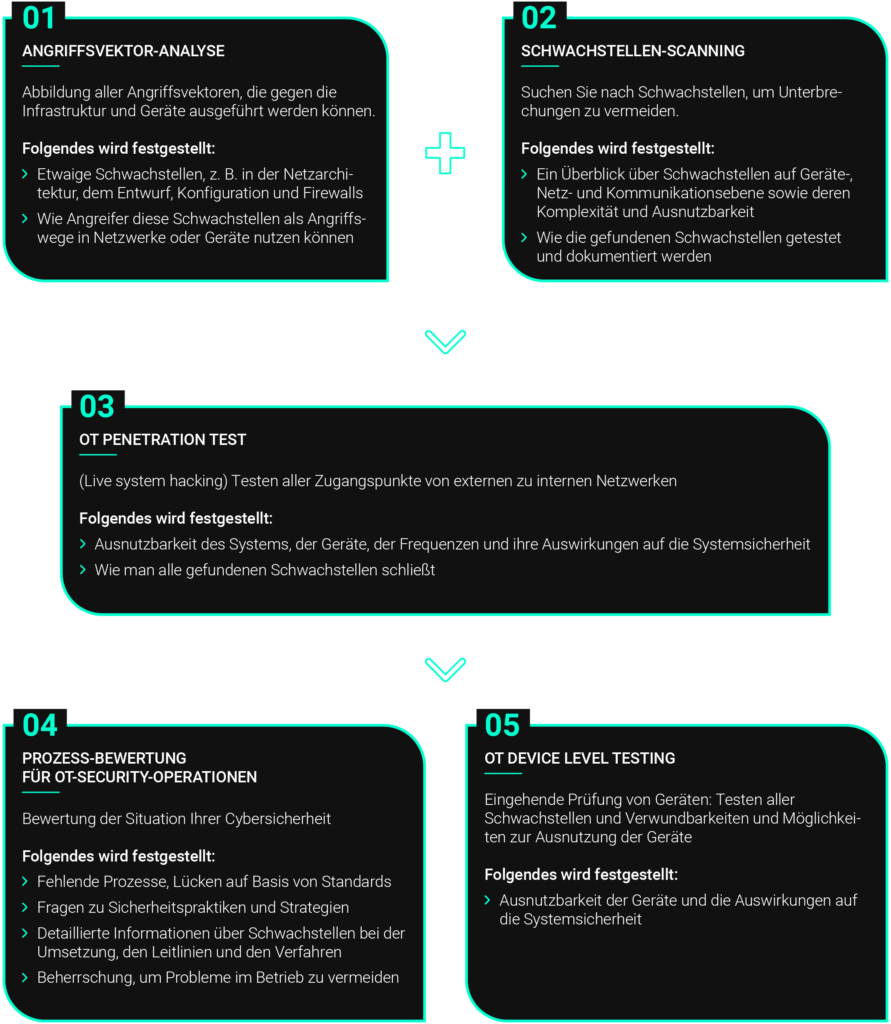
Pentesting

Modern information and communication technologies are networking the industrial world. Operational Technology (OT) such as production plants,
Control systems etc. are extremely interesting for cyber criminals. This is because the increasing automation of industrial processes
requires the networking of OT and IT technologies and thus changes the threat and risk landscape.
Where do you stand in terms of digitalisation and automation? Are your business processes protected in terms of confidentiality, availability and integrity? To check whether your OT infrastructures are also business-critical, a cyber security audit is the solution.
Are you a target for hacker attacks?
- What we offer -

Pentesting involves testing an organisation's network by hacking it in a secure manner to ensure that no external or internal threats bypass the organisation's cyber security initiatives, protocols or processes. This includes security threats such as social engineering. Social engineering takes advantage of the malleability of the human psyche. Traditional attacks utilise advanced software or low-tech initiatives such as email phishing or even planting an infected hardware device on an employee.

the advantages of an audit
Trust
The confirmation of an independent
Audits ensure that
on the basis of an OT test the
Special safety tested
and the activity of a
is subject to constant monitoring,
creates trust with the
Customers.
Competitive advantage
With a cyber security OT audit from an independent body, experts gain a competitive advantage over the competition.
Advertising material
References to a cyber security OT audit can be incorporated into communication media. For the experts, certification is a testimony to their professionalism and commitment to the availability of their production environment.